Welcome to Hawatel's blog!
April 23, 2019 | Cyber security / Infrastructure management
Citrix Netscaler and IP reputation - a way to block dangerous sources to web applications
The consequences of attacks on websites have often been the reason for lowering the impeccable reputation built over the years by many companies. In the previously published material "Web Application Protection System - shield against malicious attacks," I wrote, among other things, about threats coming from the public network - about their detrimental impact on the attacked organization. The security of systems published on the Internet can be significantly increased by implementing a solution called WAF (Web Application Firewall). The first stage of such implementation can often be completed in 2 - 4 weeks, obtaining real protection against malicious attacks. At the outset, attention is directed towards global protections that can cover all web applications in an organization without the need to delve into their operation.
IP address reputation
WAF solutions have at least several mechanisms that can be quickly and accurately activated in a production environment. One of them is the so-called "IP address reputation." This mechanism continuously updates the list of IP addresses that have conducted various types of attacks. Then, using the appropriate rule, the WAF system can effectively block access from the harmful source to web applications or send a warning and information to the user about blocking the IP address due to its bad reputation.
Webroot IP address clasification
In 2016, Citrix integrated its solution with Webroot, providing both existing and new customers with a valuable tool for blocking dangerous sources of access to websites. Using its own sensor network, Webroot detects potential harmful sources on the Internet and provides a classification, which is divided into 11 categories:
- Windows exploits - includes IP addresses that distribute malware, crafted shellcode, intrusion tools (rootkits), viruses.
- Web attacks - contains IP addresses that have historically conducted attacks on websites.
- Phishing - includes IP addresses that serve websites used for scams, phishing for specific information such as login credentials, credit card details, etc.
- Botnets - a group of servers and computers infected with malware, which can be used, for example, to send spam or to conduct organized cyberattacks.
- Denial of service - groups of IPs that execute DoS, DDOS, SYN flood attacks or exhibit unusual activity.
- Scanners - includes IP addresses that scan the Internet for vulnerabilities or conduct brute-force attacks to break passwords.
- TOR proxies - a special network providing anonymity to dishonest users accessing the Internet. It is often used to minimize the risk of detection.
- Anonymous proxies - proxy servers that mask the original IP addresses, often making it difficult to detect the user.
- Reputation - contains IP addresses infected with malware. This category also includes a list of IP addresses with a medium reputation index.
- Spam sources - list of IP addresses sending spam in the form of emails, forum posts, or other activities aimed at flooding the Internet with malicious content.
- Mobile threats - includes IP addresses of mobile devices that may have been infected with malware or deliberately used for attacks.
Webroot provides a website for manual verification of the category and reputation index of a selected IP address - BrightCloud. It also shows the individual categories assigned to a particular source.

Webroot BrightCloud Threat Intelligence
IP address categorization statistics
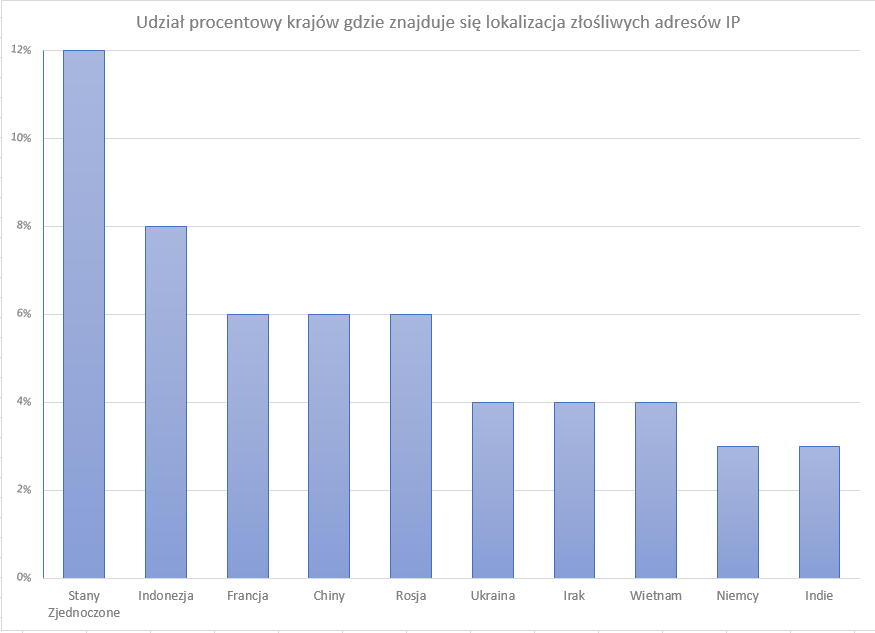
The following diagram illustrates the list of categories with the highest percentage share of malicious IP addresses in the Webroot company's database. The data comes from the 2018 Webroot Threat Report.

An interesting phenomenon is that, based on the data from this report, the highest number of malicious IP addresses was recorded in the United States - as much as 12%, as shown in the diagram.
A very important element in Webroot's IP address classification is the 5-minute refresh of the list (so-called incremental update) of dangerous sources. Static classifications that can be downloaded from the Internet are often not updated and may pose a risk of blocking addresses whose reputation index has been restored to an acceptable level.
Sources of information about dangeorus IP addresses
Using over 52 million network sensors, Webroot analyzes Internet traffic, classifying over 4.3 billion IP addresses. Webroot uses the following solutions to collect data on harmful sources:
- Semi-open proxy farms - a network of proxy servers that users can use without realizing that their activity is being monitored to detect potential attacks.
- Honeypot - an isolated area of the local network containing unprotected servers and applications but monitored for unauthorized use and attempts to exploit vulnerabilities. Attackers are unaware that they have been intentionally introduced into the local network or application.
- Spam trap - dedicated email addresses whose mailboxes are monitored to detect spam and track sources of email dissemination.
- Other sources - data may come, for example, from Internet Service Providers (ISPs) who have their solutions for tracking the activity of dangerous IP addresses.
Benefits of using IP reputation in Citrix NetScaler
The IP Reputation functionality is available to Citrix customers with a Platinum Edition license or as an option with an Enterprise Edition license. The Webroot IP address reputation mechanism is fully integrated with the Citrix Netscaler ADC/WAF solution.
The benefits of this functionality are as follows:
- Precise blocking of connections to applications originating from dangerous IP addresses.
- The list of dangerous sources, updated every 5 minutes, can be quickly activated for multiple applications simultaneously.
- Relieving application servers from processing requests from dangerous IP addresses.
- IP address reputation can verify both source and destination IP addresses of connections.
- The solution is supported in High Availability, Cluster, forward proxy, and reverse proxy configurations.
- Quick adaptation of the solution in a production environment.
More information about the IP Reputation solution can be found in the Citrix documentation or by contacting the author directly.
Sources:
- Webroot 2018 Threat Report
- BrightCloud IP Reputation Service
- Citrix Netscaler ADC Product Documentation